News
Optimizing and troubleshooting Outlook for Mac OS X
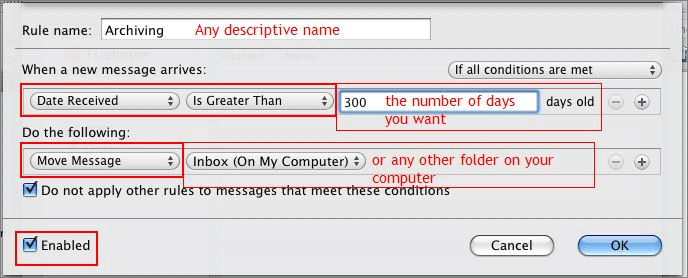
I’m a Mac user. And Outlook for Mac makes me sad. That’s because, when compared to its Windows counterpart, Outlook for OS X (aka Outlook 2011) is an underperformer. Maybe it’s because the Windows version was built in the same shop as the Exchange service. Or maybe...
What healthcare companies can learn from Anthem’s data breach
If you’ve followed the news behind Sony, JP Morgan and other highly publicized breaches, you’ll notice that this latest Anthem breach follows a very familiar trend. Corporate IT systems are fighting a losing battle against today’s hackers. Unfortunately, when it comes...
Massive password hacks: How SSO makes it easier to cope
On Tuesday, a U.S. security firm uncovered that a group stole 1.2 billion Internet user credentials in what is being called the largest security breach in recent history. If you’ve seen the news coverage of this story, you’ve probably heard experts tell you to change...
Upgrade to IP: Using Technology to Do More for Your Business
As a business owner, you understand the importance of keeping your business software programs current with the latest updates and upgrades in order to keep your company competitive. But how long has it been since you updated your phone system? Phone systems are often...
When strategic business assets fail
According to analysts, the loss of a business-critical application service such as email could cost an organization in the region of $ 1,000 per minute – more than a million dollars per day – while the impact of data center downtime, brought about by a corporate-wide...
How to compare UPS Systems
Having reviewed a lot of UPS ads out there, it is clear that some guidance on how to choose the most appropriate UPS System, and more importantly how to compare one UPS system against another. Firstly, technology – generally speaking an online double conversion UPS is...
Integrating UC and CRM: Make Your Customer Records Do Double Duty
Integration is a powerful concept. When solutions that organize and monetize your business, such as Customer Relationship Management (CRM) applications and unified communications systems (UC), are integrated together, you get more productivity out of each of those...
Making Mobility Work For You
The "Bring Your Own Device" (BYOD) phenomenon that is capturing the attention of business owners in organizations of all sizes is even more relevant for SMBs that are constantly looking for ways to reduce expenses and "do more with less." With employees leading the...
Top 5 Keys To Secure Cloud Deployment
Here are five of the most important components of any secure cloud services deployment. For many businesses, cloud services pose both a great opportunity and a major challenge. The benefits of this technology are, by this point, fairly well established: With the...
10 Steps to a Successful VoIP Rollout
VoIP (Voice over Internet Protocol) phone systems vary greatly in their features, capabilities, size, form factor, service connectivity, cabling, phone sets, etc. The technology has evolved greatly over the past decade, yet the fundamentals of IP PBX systems — such as...
It’s Storm Season: If Your Backup Solution Fails Tonight – What Is The Plan To Recover?
Is backing up the last thing on your to-do list? This task may be one of the most despised in all of IT, but that's not an excuse to leave your data in a vulnerable state. Backup needs to be inclusive and consistent. You never know when a cyber attack, natural...
Network Discovery – If You Can’t See It, You Can’t Manage It
Network discovery is the process of identifying devices attached to a network. It establishes the current state and health of your IT infrastructure. It’s essential… without visibility into your entire environment you can’t successfully accomplish even the basics of...